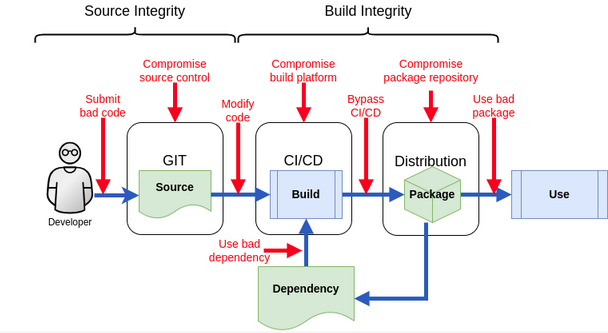
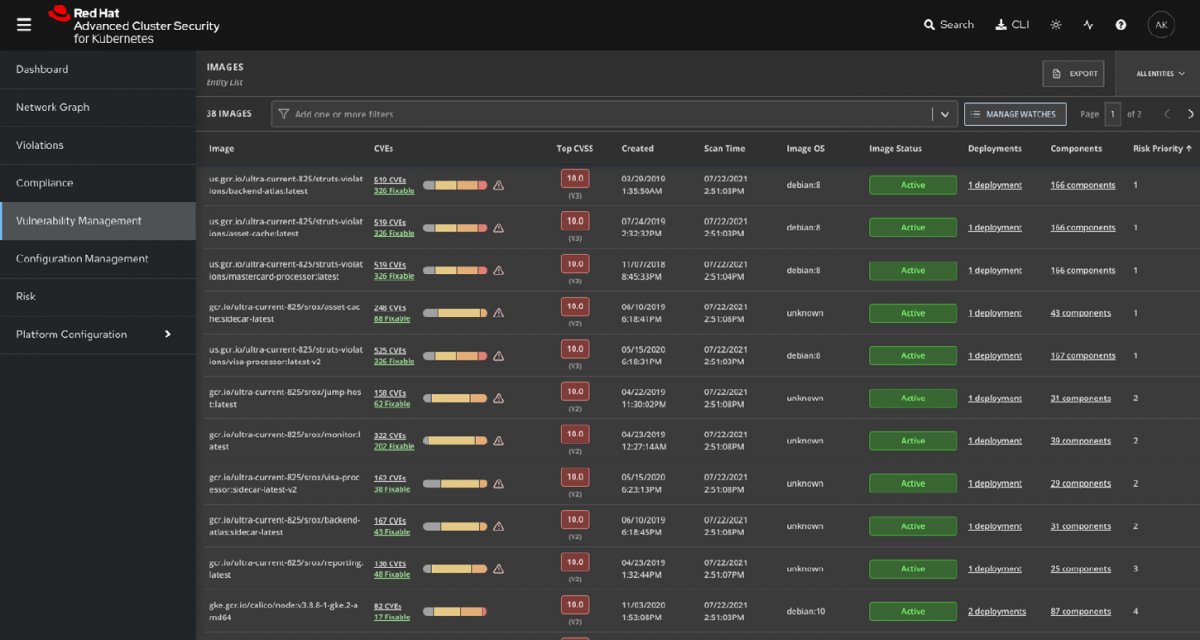
ˈpætɚns Probably almost every time we are starting to understand and to solve a general problem, we will ask ourselves, am I the first one who is facing that problem, or have there been others who in the end either failed or succeeded. This is particularly true, if I am highly uncertain whether my own […]