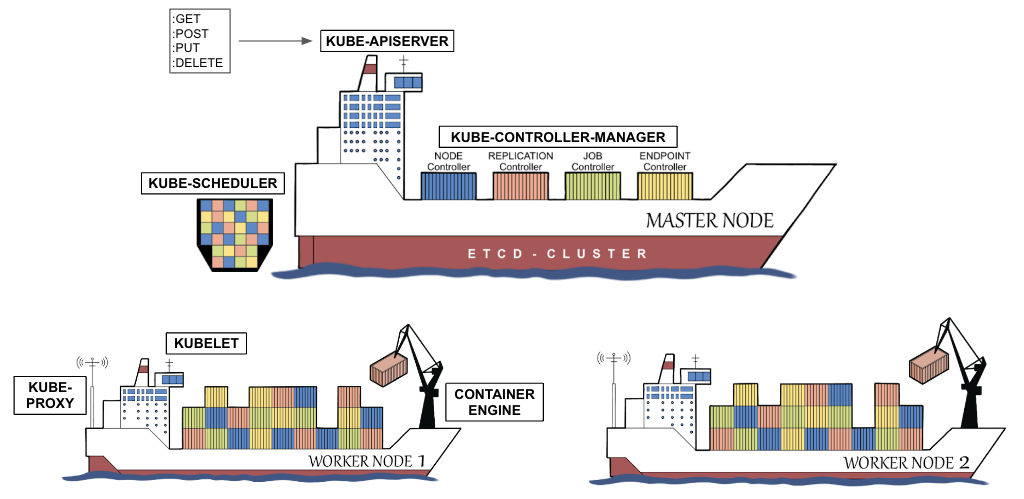
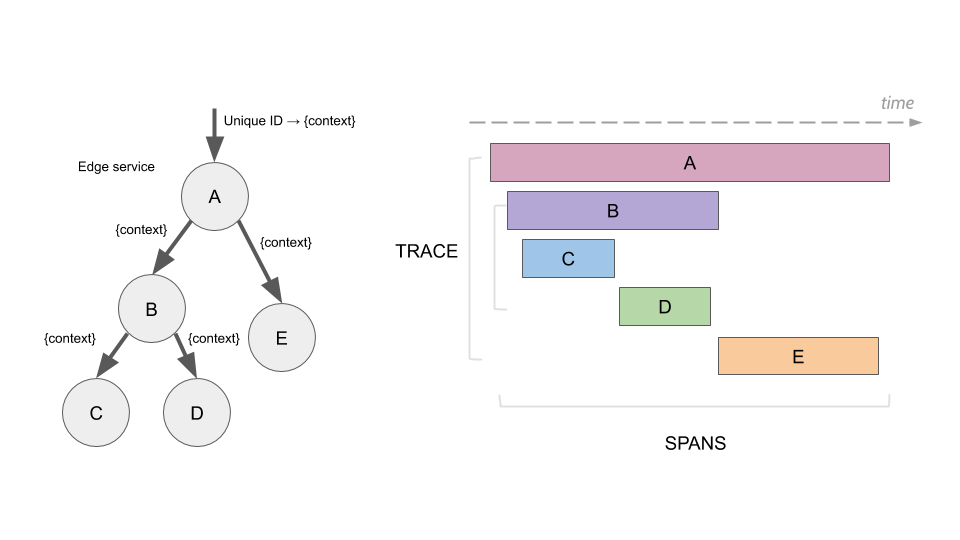
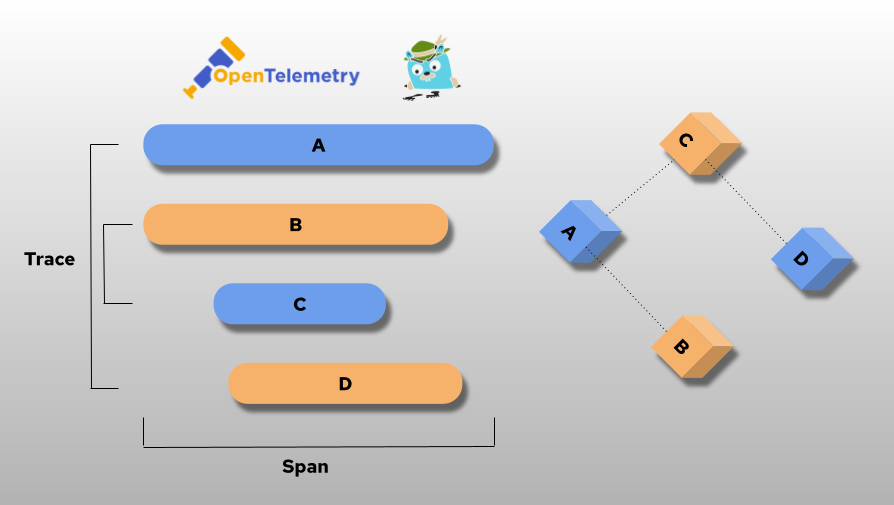
When I try to look into the future, what would I see for a datacenter? What are the requirements the data centers need to comply with? What can a solution look like? In the coming text I will try to give answers to those questions. Executive summary In the coming years the usage of services […]