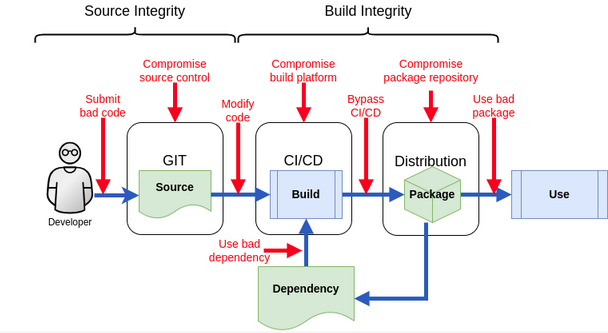
Introduction Since my last exploration of the topic in mid-2021, there have been significant advancements in cold disaster recovery for applications on Kubernetes. Since then, there have been remarkable improvements in both the technical aspects and the user experience of cold disaster recovery. Notably, the Kubernetes operator that manages the technical infrastructure for cold disaster […]