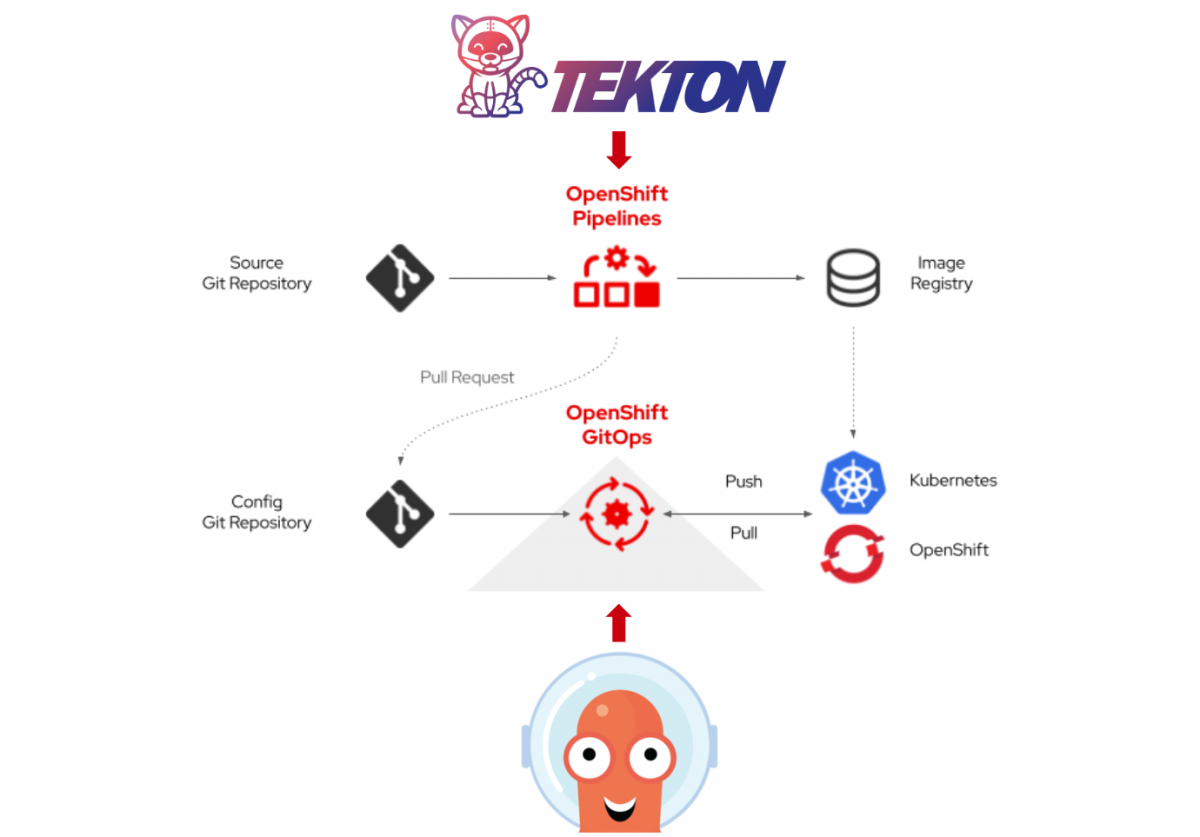
OpenSourcerers 2022 is a wrap! It was packed with interesting articles covering a wide range of topics. There are 52 articles available covering high level topics down to the dirty technical details of using Red Hat’s products and other OpenSource technologies. Your Opensourcerers blog editors followed along of course! As we come from varying backgrounds […]